Data management:
from discovery through automation
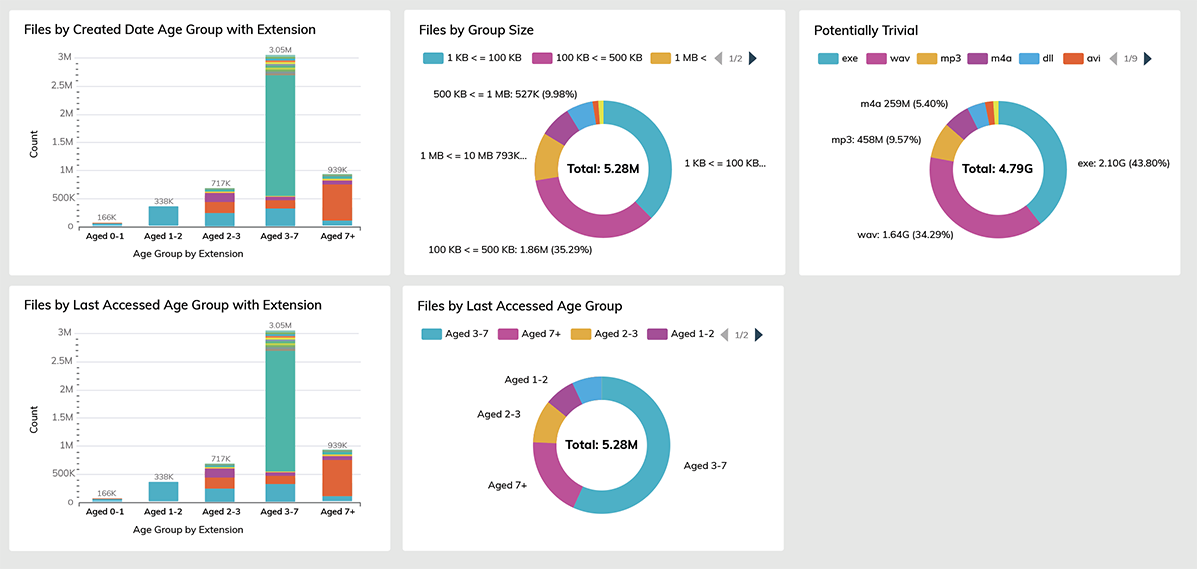
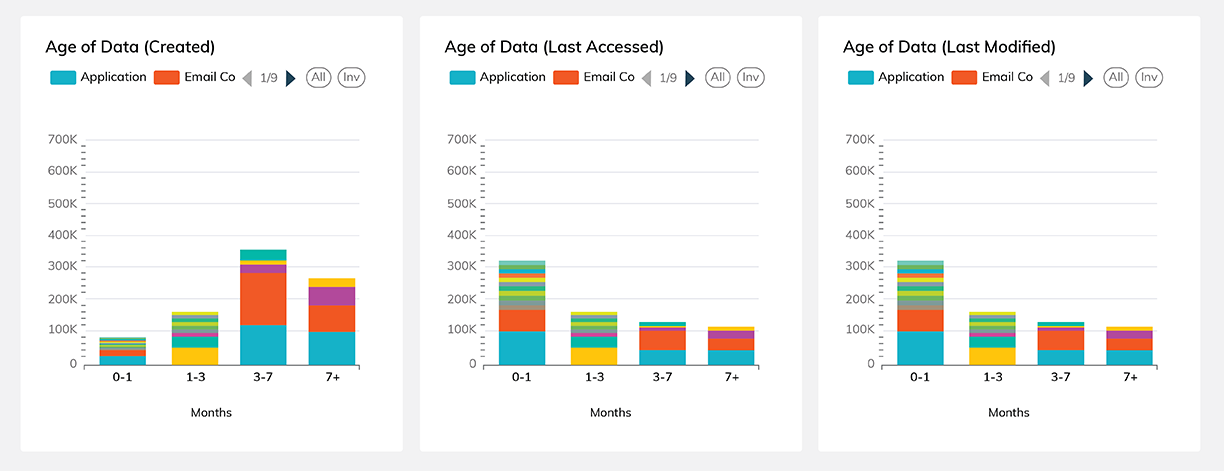
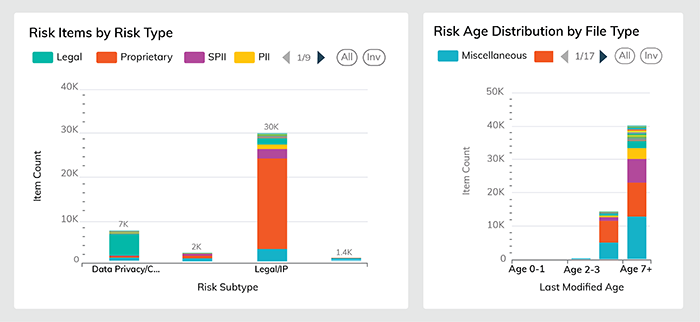
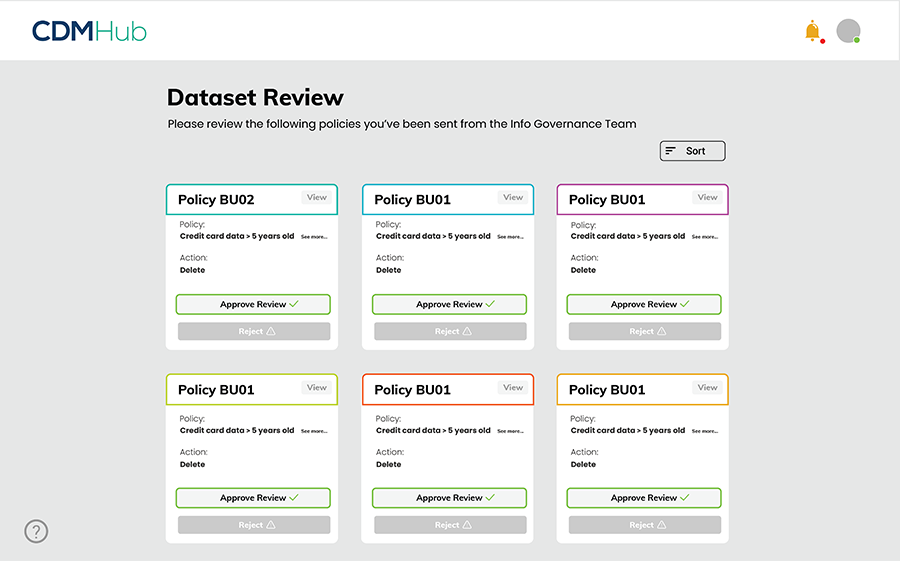
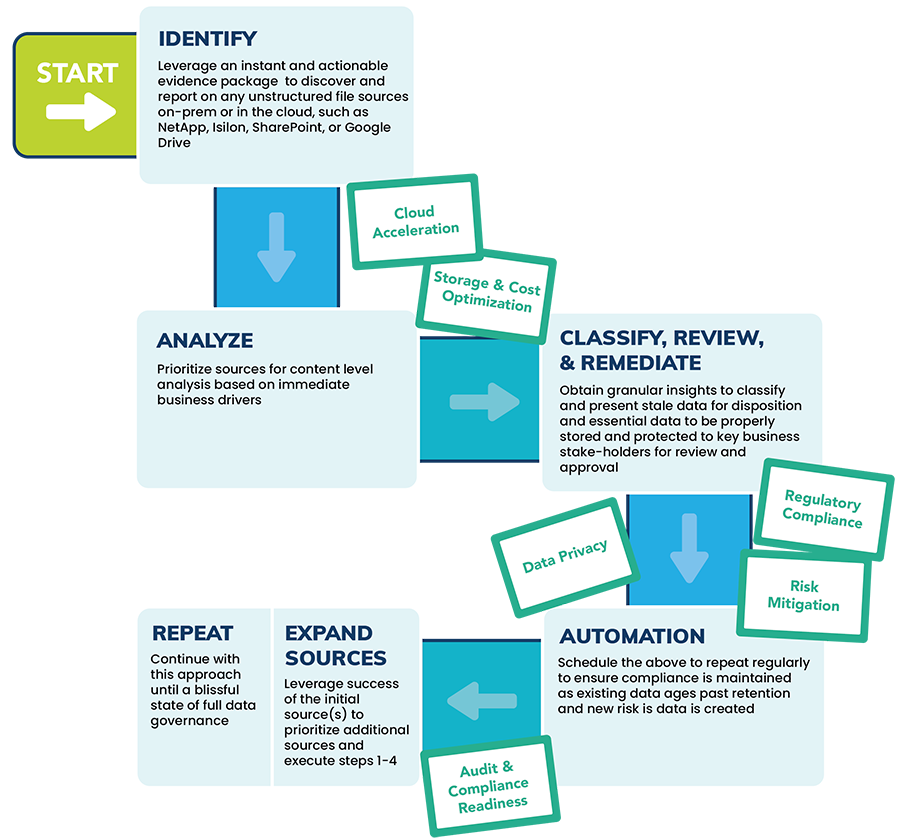
Centralize data management by rapidly identifying, normalizing, and classifying data across on-prem and cloud sources – allowing you to protect data that strengthens a business and remediate the data that weakens it.