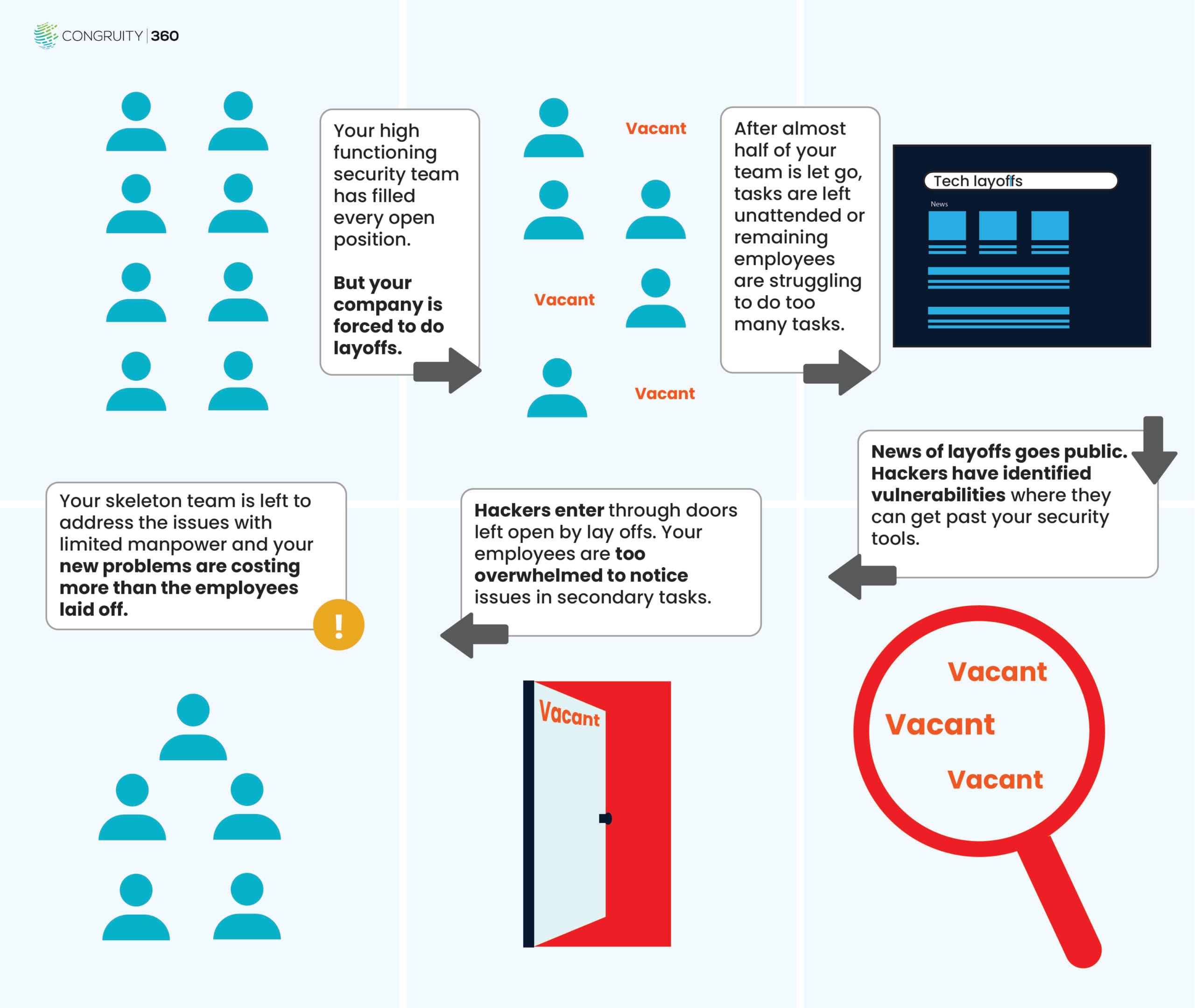
In times of financial strain, organizations often turn to layoffs as a way to cut costs. But as a recent Media Trust report shows, that very strategy may be leaving companies dangerously exposed. According to their analysis, cyberattacks against U.S. federal networks surged by 85% following the government shutdown, as threat actors exploited reduced staffing and heightened vulnerability. (Dark Reading)
If attackers are watching the public sector, imagine how much more perilous the situation can get for companies under similar stress. When teams shrink, security oversight weakens — and adversaries know this.
Why Layoffs Make Companies Attractive to Hackers
1. Less People Watching the Gates
- Reduced monitoring and response capacity: When security teams shrink, there’s less manpower to spot anomalies, investigate alerts, or respond to incidents.
- Knowledge gaps: Layoffs often cut experienced staff. Important tribal knowledge about systems, architecture, and risk may walk out the door.
- Delayed updates and patching: With fewer engineers or IT folks, critical security updates and system hardening efforts can slow down — giving attackers more time to find and exploit unpatched vulnerabilities.
2. Financial Strain Creates Social Engineering Opportunities
Media Trust’s report highlights that many of the attacks following the federal shutdown were targeted phishing campaigns aimed at financially stressed employees. (TrollEye Security) Hackers used promises of income, debt relief, or temporary work — playing on real-world anxiety to lure in victims. (TrollEye Security)
Layoffs make these social-engineering tactics far more effective, especially when morale is low and people are scrambling for new opportunities or struggling financially.
3. Deferred Security Projects & Technical Debt
Companies under cost pressure may freeze or delay investments in core security functions — things like vulnerability scanning, identity and access management (IAM), monitoring platforms, and zero-trust architecture. While these seem like discretionary in the short term, attackers view deferred security as a golden opportunity.
The Data Problem: ROT Is Your Silent Liability
Beyond people, data itself can become a huge risk factor — especially when it’s poorly managed.
- According to the Veritas Global Databerg Report, up to 85% of stored data is either dark (unknown value) or ROT — redundant, obsolete, or trivial. (Veritas)
- Specifically, 33% of data is categorized as ROT. (DQ)
- According to Diskover, unmanaged ROT data costs organizations significantly by bloating storage, complicating compliance, and creating hidden security risk. (diskoverdata.com)
Why is ROT dangerous? Because:
- It’s often ungoverned — no clear owner, no retention policy, no audit trail.
- It can contain stale credentials, forgotten PII, or legacy access paths.
- Rotting data increases attack surface — the more you store (especially data you don’t even understand), the more likely something valuable is hiding in plain sight.
The Cost of Storing Data: It’s Not Free
Storing data — especially at scale — has real costs, and these multiply when a large portion is ROT.
- According to Diskover, the cost of ROT data is nontrivial: for a 1 PB (petabyte) dataset, unmanaged ROT can run into hundreds of thousands of dollars annually. (diskoverdata.com)
- Backup and enterprise storage cost per terabyte (TB) varies: Zmanda reports annual costs from $300 to $2,500 per TB, depending on licensing, deduplication, and storage architecture. (Zmanda)
- On the cloud side, storage costs can also add up: for instance, standard object storage pricing on major cloud platforms can be in the range of $0.01–$0.02 per GB/month depending on the tier. (Finout)
When you’re storing ROT, you’re essentially burning money to keep data that doesn’t help you — but could help attackers. It may seem easier to purchase security tools to protect all of your data, but the fact of the matter is: more data + more security tools = expensive.
How a Data Management Program Can Protect You and Save Money
Given these compounded risks, what can companies do? The answer lies in a strategic data-management program that does two things:
- Reduce Attack Surface
- Data classification: Identify and categorize data by sensitivity, access patterns, and value.
- Disposition and archiving: Move “cold” or non-critical data to deeply archived tiers or delete it if it serves no business purpose.
- Defensible deletion: Implement policies and workflows to safely remove ROT data, with audit trails.
- Data classification: Identify and categorize data by sensitivity, access patterns, and value.
- Lower Costs & Reinforce Security
- Tiered storage: Use cost-optimized storage for low-access (archival) data and keep high-sensitivity, high-access data in more secure but more expensive tiers.
- Deduplication and compression: Modern data platforms can significantly reduce storage size, lowering per-TB costs.
- Access controls and monitoring: Apply identity access management, encryption, and monitoring to data based on classification — so only the right people can reach sensitive data.
- Automated remediation: When you detect stale data or ROT, automate its lifecycle (archive, quarantine, or purge) so the cleanup doesn’t drain staff time.
- Tiered storage: Use cost-optimized storage for low-access (archival) data and keep high-sensitivity, high-access data in more secure but more expensive tiers.
With a program in place, companies not only make themselves less attractive to attackers but free up storage budget — potentially reducing the pressure that triggers layoffs in the first place.
Why This Matters Now
- The Media Trust data makes one thing clear: attackers respond to weakness. Layoffs, shutdowns, and understaffed security teams don’t go unnoticed. (Dark Reading)
- Left unchecked, ROT data becomes a ghost asset — invisible to you, but ripe for exploitation.
- A data management program is not just a cost center — it’s a force-multiplier: securing data, cutting waste, and preserving headcount by reducing unnecessary spending.
Protect your company during layoffs
Layoffs might feel like a quick way to save money, but they can dramatically increase your cybersecurity risk. When people leave, vulnerabilities can linger. When data is unmanaged, risk multiplies. But by putting in place a holistic data-management strategy — one that classifies, archives, and removes unnecessary data — you can:
- Shrink your attack surface
- Lower your storage costs
- Improve your security posture
- And potentially reduce the need for future cost-cutting layoffs
If you’re ready to build resilience (without sacrificing security under financial pressure), a proactive data hygiene program could be one of your smartest investments: start now.