Operationalize NIST 2.0 Strengthen Governance, Reduce Risk
With the introduction of Governance into the NIST 2.0 Cybersecurity Framework, alignment now requires more than technical security – it demands full visibility and control over your data. We help Security & GRC leaders operationalize these requirements — giving you visibility across your data landscape, automating governance policies, and closing the gaps that put your organization at risk.
Connect With Our Team to Get Aligned with NIST 2.0!
Schedule a 30-minute intro call with our team!
Identify
Catalog, Organize, and Classify Data
Govern
Create Automated Data Governance Policies
Protect
Remediate Identified Sensitive Data Issues
The New NIST 2.0 Cybersecurity Framework Raises the Bar with a Focus on Governance
NIST 2.0 introduces a new category focused on Governance, expanding cybersecurity beyond technology and into how organizations manage, protect, and make decisions about data. To align, leaders must move from tactical controls to strategic visibility—understanding what data exists, where it lives, who has access, and how it’s governed.
IDENTIFY
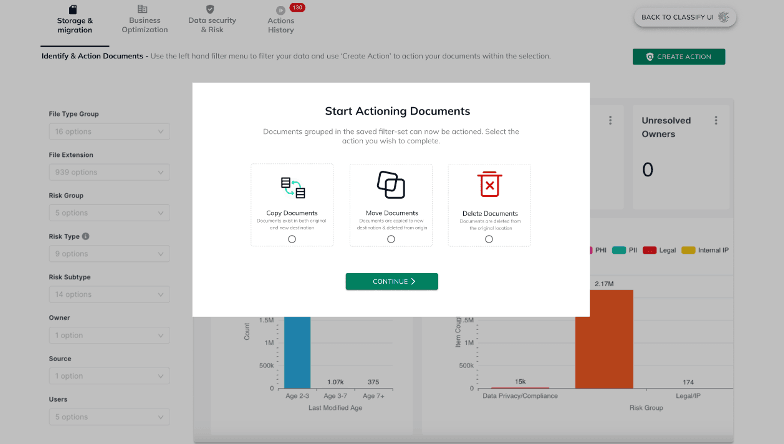
Identify data based on attributes like redundant data, obsolete data, trivial data, PII/PHI, data by owner, and data with open read/write access.
Take strategic actions on this data to:
- Reduce attack surface, increase efficiency, save money
- Move data to secure landing zones to reduce access for improved security posture and control
- Eliminate orphaned files and ensure data is managed and can adhere to policy enforcement
- Identify gaps in access permissions
GOVERN
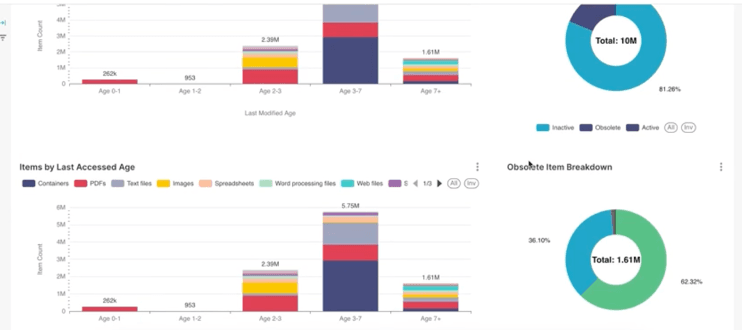
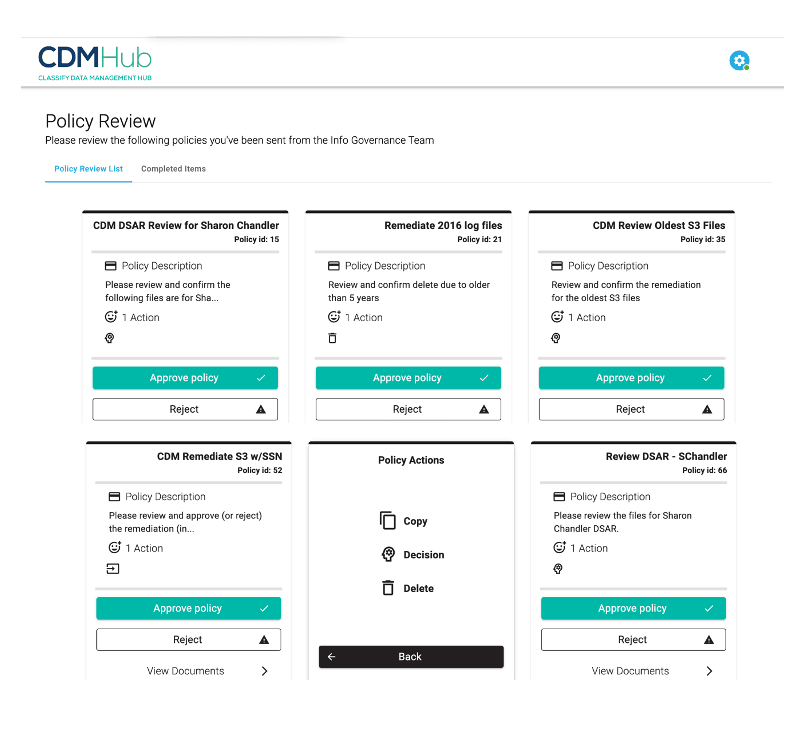
Ensure data is categorized, classified, and managed according to defined policies and procedures. Enforce record retention, access control, and exception handling.
- Policy driven culling of data reduces attack surface
- Defined access controls based upon data value and risk mitigation
- Data security policies are more consistently applied and monitored
PROTECT
Provide the ability to efficiently manage the right data with the right access permissions.
- Proper access controls are maintained, reducing cyber attack data entry points
- Privileged network strategy dramatically improves defense from cyber attacks and can reduce overall attack surface by 50%+
- Eliminate gaps in active management of data to stop Threat Actors from unmonitored access into the data estate