Strengthen Cyber Resilience, Reduce Storage Costs with NetGap
Congruity360’s NetGap is the smarter, safer way to handle inactive, redundant, or trivial (ROT), and other potentially sensitive data—helping you meet modern NIST cybersecurity guidance that prioritizes data visibility, governance, and risk reduction. Instead of letting low-value information that could contain risk sit inside your production environment—where it expands your attack surface and inflates storage and backup costs—NetGap securely moves it to a privileged, isolated network.
Reduce Attack Surface by 50%+
Move sensitive, inactive data off production. Isolate in a privileged network.
Cut Infrastructure & Backup Costs
Significant savings achieved from Tier 1 storage and backup reduction.
Align with NIST CSF 2.0 Standards
Limits data access and provides an efficient and safe way to recover data post cyber attack.
Identify Target NetGap Data
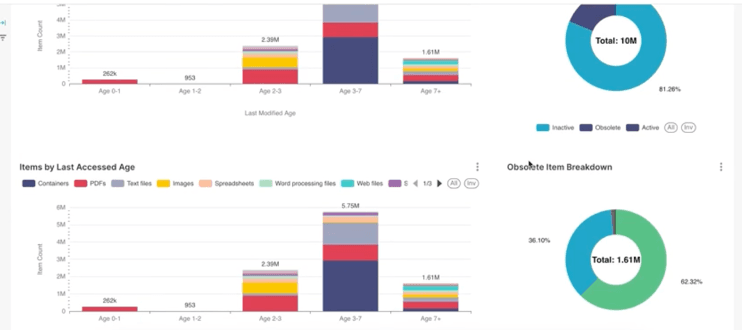
NetGap is designed to provide a safe location for inactive data that is currently being stored in your production environment. The first step is to identify the data suitable for NetGap using the Enterprise Insights solution to scan the data and analyze key metrics such as data access, age, ownership and potential risk.
Once the target data has been identified, it can be flagged for migration into the NetGap environment.
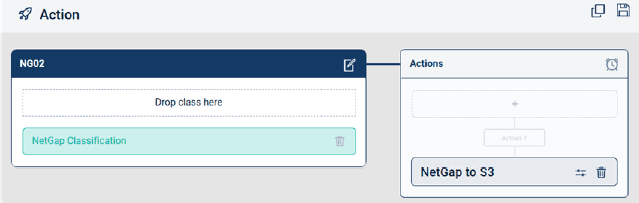
Migrate Data to NetGap Environment
The NetGap process allows uses to create a policy to migrate the target data from the production environment to the NetGap protected environment. NetGap migrates the file to the new privileged network storage and leaves behind a dynamic link.
Recover Data Via Secure Links
If a user clicks on a file that has been migrated, they will receive an alert to provide a reason for the request to access the data. This triggers a request to the ticketing system that includes the request, reason for the request, and the original location for the restore to follow – if approved, the file is returned.

NetGap Aligns with Core NIST 2.0 Pillars
While the broader Congruity360 platform supports all six NIST 2.0 functions—Identify, Govern, Protect, Detect, Respond, and Recover—NetGap is purpose-built to strengthen three of these pillars:
Govern
NetGap limits unnecessary access to inactive or low-value data, helping organizations remediate audit findings, enforce least-privileged controls, and demonstrate stronger governance over unstructured data.
Protect
By securely isolating redundant or inactive data into a privileged network, NetGap shrinks your exposed attack surface—making it harder for threat actors to discover, move laterally to, or exploit this data.
Recover
With data organized and isolated in a clean, controlled environment, NetGap provides a more efficient and safer path to recovery following a breach, ensuring that critical information can be restored without reintroducing unnecessary risk.

